Global Embedded Security Market: By Offering, By Security Type, By Application, By Region & Segmental Insights Trends and Forecast, 2024 – 2034
- Industry: Technology
- Report ID: TNR-110-1113
- Number of Pages: 420
- Table/Charts : Yes
- May, 2024
- Base Year : 2024
- No. of Companies : 10+
- No. of Countries : 29
- Views : 10234
- Covid Impact Covered: Yes
- War Impact Covered: Yes
- Formats : PDF, Excel, PPT
Embedded security refers to the implementation of protective measures within embedded systems, which are specialized computing devices designed for specific control functions within larger systems. These systems are ubiquitous in modern technology, found in everything from household appliances and medical devices to industrial machines and automotive systems. Embedded security aims to safeguard these devices against unauthorized access, cyber threats, and data breaches by integrating hardware and software defenses directly into the system’s design.
This includes secure boot processes, encryption, authentication protocols, and intrusion detection mechanisms. Ensuring embedded security is critical because these systems often operate in environments where they are exposed to various physical and digital vulnerabilities. Effective embedded security not only protects sensitive information and ensures the reliable operation of critical systems but also helps maintain user trust and compliance with regulatory standards. As embedded systems continue to proliferate, the importance of robust security measures becomes increasingly paramount to prevent potential exploitation and disruption.
The demand for embedded security is driven by the increasing proliferation of IoT devices, smart technologies, and the need for secure industrial control systems, all of which require robust protection against escalating cyber threats. Key drivers include the growing incidence of cyberattacks, regulatory requirements for data protection, and the need for secure communication in connected devices.
However, the implementation of embedded security faces restraints such as the complexity of integrating advanced security features into constrained environments with limited processing power and memory, as well as the additional costs and development time. The advent of 5G technology, advancements in AI and machine learning for threat detection, and the increasing adoption of cloud services provide avenues for enhanced security solutions. Moreover, the ongoing evolution of regulatory frameworks and industry standards for cybersecurity further propels innovation and investment in embedded security, making it a critical focus for future technological development.
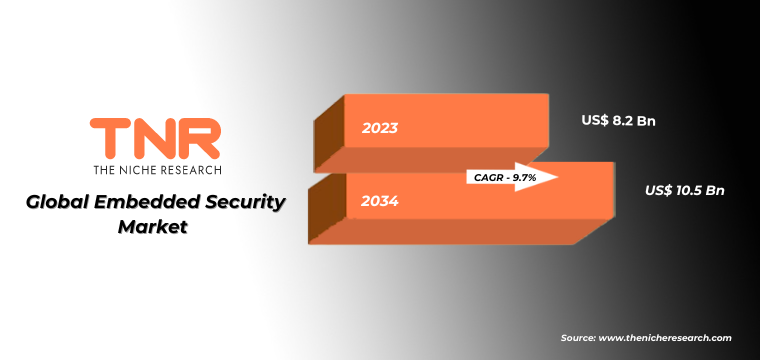
In terms of revenue, the global embedded security market was worth US$ 8.2 Bn in 2023, anticipated to witness CAGR of 9.7% During 2024 – 2034.
Global Embedded Security Market: Key Factors
Proliferation of IoT Devices: The widespread adoption of Internet of Things (IoT) devices in consumer, industrial, and healthcare sectors drives the need for robust security measures to protect sensitive data and ensure device integrity. Increasing cyberattacks on embedded systems necessitate advanced security solutions to safeguard critical infrastructure and personal data.
Regulatory Compliance: Stringent regulations and standards, such as GDPR, HIPAA, and industry-specific guidelines, compel organizations to implement strong security measures. Innovations in AI, machine learning, and 5G technology enhance security capabilities, making it easier to detect and mitigate threats in real-time.
Emerging Markets: Growth in emerging markets offers significant opportunities for the expansion of embedded security solutions as these regions adopt more connected technologies. Ongoing improvements in encryption technologies provide new methods to secure data in embedded systems, enhancing overall security.
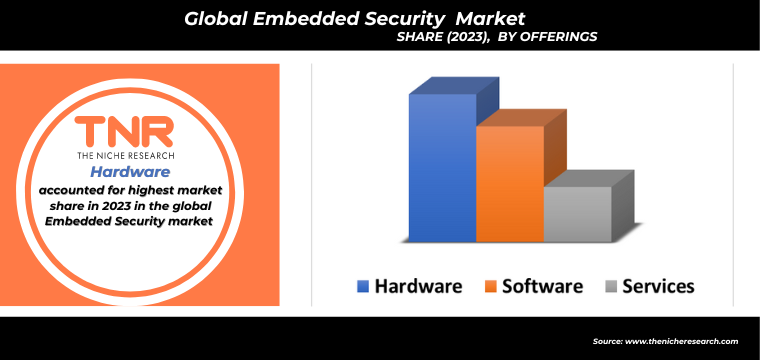
Hardware Segment Has Garnered Major Market Share in the Global Embedded Security Market During the Forecast Period (2024 – 2034).
The demand for hardware in the embedded security market is driven by several key factors, reflecting the increasing need for robust and reliable security solutions across various applications. Firstly, the exponential growth of IoT devices necessitates secure hardware to protect against cyber threats and ensure device integrity. This is particularly crucial in sectors like healthcare, automotive, and industrial automation, where security breaches can have severe consequences.
Additionally, regulatory requirements and compliance standards mandate the implementation of secure hardware components, such as trusted platform modules (TPMs) and hardware security modules (HSMs), to safeguard sensitive data. Technological advancements in areas such as 5G, artificial intelligence, and machine learning further enhance the capabilities of security hardware, making it more efficient and effective. The increasing complexity and sophistication of cyberattacks also drive the need for advanced hardware-based security solutions, which can offer more robust protection than software-only approaches. As a result, the demand for secure and innovative hardware continues to grow, underpinning the broader embedded security market.
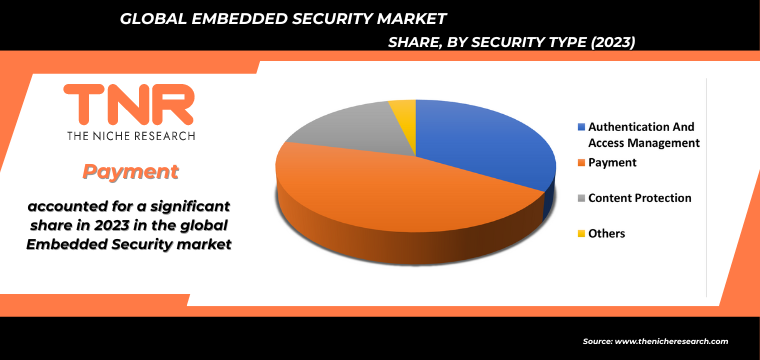
By Security Type Payment Segment had the Highest Share in the Global Embedded Security Market in 2023.
The embedded security market in the payment sector is driven by the increasing need to protect financial transactions and sensitive user data from sophisticated cyber threats. As digital payment methods, such as contactless payments, mobile wallets, and online banking, become more prevalent, the demand for secure embedded solutions rises. Key security types include secure elements (SE), trusted execution environments (TEE), and hardware security modules (HSM), which ensure the integrity and confidentiality of payment information.
Regulatory compliance, such as PCI-DSS standards, also compels financial institutions and payment service providers to adopt robust embedded security measures. Additionally, the growing consumer awareness about data privacy and the rising incidence of financial fraud drive the need for enhanced security in payment systems. Technological advancements, such as biometrics and tokenization, further bolster the demand for sophisticated embedded security solutions, ensuring secure and seamless payment experiences. Consequently, the need to protect digital financial transactions continues to propel the embedded security market in the payment sector.
By Application Smart Identity Cards Segment had the Highest Share in the Global Embedded Security Market in 2023.
The demand for embedded security in smart identity cards is driven by the increasing need for secure and reliable identification solutions in various sectors, including government, healthcare, and finance. Smart identity cards, equipped with embedded security features like encryption, secure elements (SE), and biometric authentication, are essential for protecting personal information and ensuring the authenticity of the cardholder’s identity. The rise in identity theft and data breaches underscores the necessity for advanced security measures, prompting governments and organizations to adopt smart identity cards.
Additionally, regulatory requirements for enhanced security in identity verification processes, such as e-passports and national ID programs, further fuel this demand. Technological advancements in chip technology and cryptographic methods enhance the security and functionality of these cards, making them more resilient to tampering and fraud. As digital transformation accelerates and the need for secure personal identification grows, the embedded security market for smart identity cards continues to expand, driven by the imperative to safeguard sensitive information and prevent unauthorized access.
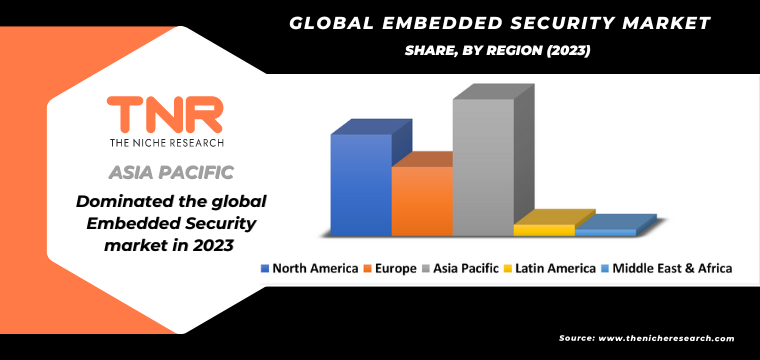
The demand for embedded security in the Asia-Pacific region is driven by rapid technological advancements, increasing digital transformation, and heightened awareness of cybersecurity threats.
The proliferation of IoT devices, smart cities, and industrial automation in countries like China, Japan, and South Korea necessitates robust embedded security solutions to protect sensitive data and critical infrastructure. Additionally, the region’s growing financial services sector, with the widespread adoption of digital payment systems, underscores the need for secure hardware and software to prevent cyber fraud and data breaches.
Government regulations and initiatives aimed at strengthening cybersecurity frameworks further propel the demand for embedded security. For instance, policies mandating secure authentication and data protection in connected devices and critical systems are becoming more prevalent. The increasing consumer demand for secure digital services, coupled with the expansion of the IT and telecommunications industries, ensures that embedded security remains a priority, driving substantial growth in the Asia-Pacific market.
Competitive Landscape: Global Embedded Security Market:
- IDEMIA
- Infineon
- Microchip Technology
- NXP
- Qualcomm
- Renesas
- Samsung
- STMicroelectronics
- Texas Instruments
- Thales Group
- Other Industry Participants
Global Embedded Security Market: Key Insights
| Report Specifications | Details |
| Market Revenue in 2023 | US$ 8.2 Bn |
| Market Size Forecast by 2034 | US$ 10.5 Bn |
| Growth Rate (CAGR) | 9.7% |
| Historic Data | 2016 – 2022 |
| Base Year for Estimation | 2023 |
| Forecast Period | 2024 – 2034 |
| Report Inclusions | Market Size & Estimates, Market Dynamics, Competitive Scenario, Trends, Growth Factors, Market Determinants, Key Investment Segmentation, Product/Service/Solutions Benchmarking |
| Segments Covered | By Offering, By Security Type, By Application |
| Regions Covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
| Countries Covered | U.S., Canada, Mexico, Rest of North America, France, The UK, Spain, Germany, Italy, Nordic Countries (Denmark, Finland, Iceland, Sweden, Norway), Benelux Union (Belgium, The Netherlands, Luxembourg), Rest of Europe, China, Japan, India, New Zealand, Australia, South Korea, Southeast Asia (Indonesia, Thailand, Malaysia, Singapore, Rest of Southeast Asia), Rest of Asia Pacific, Saudi Arabia, UAE, Egypt, Kuwait, South Africa, Rest of Middle East & Africa, Brazil, Argentina, Rest of Latin America |
| Key Players | IDEMIA, Infineon, Microchip Technology, NXP, Qualcomm, Renesas, Samsung, STMicroelectronics, Texas Instruments, Thales Group, Other Industry Participants |
| Customization Scope | Customization allows for the inclusion/modification of content pertaining to geographical regions, countries, and specific market segments. |
| Pricing & Procurement Options | Explore purchase options tailored to your specific research requirements |
| Contact Details | Consult With Our Expert
Japan (Toll-Free): +81 663-386-8111 South Korea (Toll-Free): +82-808- 703-126 Saudi Arabia (Toll-Free): +966 800-850-1643 United Kingdom: +44 753-710-5080 United States: +1 302-232-5106 E-mail: askanexpert@thenicheresearch.com
|
Global Embedded Security Market
By Offering
- Hardware
- Secure Element
- Embedded SIM
- Trusted Platform Modules
- Hardware Security Modules
- Hardware Token
- Software
- Services
By Security Type
- Authentication And Access Management
- Payment
- Content Protection
- Others
By Application
- Wearables
- Smartphones
- Automotive
- Smart Identity Cards
- Industrial
- Payment Processing and Card
- Others
By Region
- North America (U.S., Canada, Mexico, Rest of North America)
- Europe (France, The UK, Spain, Germany, Italy, Nordic Countries (Denmark, Finland, Iceland, Sweden, Norway), Benelux Union (Belgium, The Netherlands, Luxembourg), Rest of Europe)
- Asia Pacific (China, Japan, India, New Zealand, Australia, South Korea, Southeast Asia (Indonesia, Thailand, Malaysia, Singapore, Rest of Southeast Asia), Rest of Asia Pacific)
- Middle East & Africa (Saudi Arabia, UAE, Egypt, Kuwait, South Africa, Rest of Middle East & Africa)
- Latin America (Brazil, Argentina, Rest of Latin America)
Report Layout:
Table of Contents
**Exclusive for Multi-User and Enterprise User.
Global Embedded Security Market
By Offering
- Hardware
- Secure Element
- Embedded SIM
- Trusted Platform Modules
- Hardware Security Modules
- Hardware Token
- Software
- Services
By Security Type
- Authentication And Access Management
- Payment
- Content Protection
- Others
By Application
- Wearables
- Smartphones
- Automotive
- Smart Identity Cards
- Industrial
- Payment Processing and Card
- Others
By Region
- North America (U.S., Canada, Mexico, Rest of North America)
- Europe (France, The UK, Spain, Germany, Italy, Nordic Countries (Denmark, Finland, Iceland, Sweden, Norway), Benelux Union (Belgium, The Netherlands, Luxembourg), Rest of Europe)
- Asia Pacific (China, Japan, India, New Zealand, Australia, South Korea, Southeast Asia (Indonesia, Thailand, Malaysia, Singapore, Rest of Southeast Asia), Rest of Asia Pacific)
- Middle East & Africa (Saudi Arabia, UAE, Egypt, Kuwait, South Africa, Rest of Middle East & Africa)
- Latin America (Brazil, Argentina, Rest of Latin America)
The Niche Research approach encompasses both primary and secondary research methods to provide comprehensive insights. While primary research is the cornerstone of our studies, we also incorporate secondary research sources such as company annual reports, premium industry databases, press releases, industry journals, and white papers.
Within our primary research, we actively engage with various industry stakeholders, conducting paid interviews and surveys. Our meticulous analysis extends to every market participant in major countries, allowing us to thoroughly examine their portfolios, calculate market shares, and segment revenues.
Our data collection primarily focuses on individual countries within our research scope, enabling us to estimate regional market sizes. Typically, we employ a bottom-up approach, meticulously tracking trends in different countries. We analyze growth drivers, constraints, technological innovations, and opportunities for each country, ultimately arriving at regional figures.Our process begins by examining the growth prospects of each country. Building upon these insights, we project growth and trends for the entire region. Finally, we utilize our proprietary model to refine estimations and forecasts.
Our data validation standards are integral to ensuring the reliability and accuracy of our research findings. Here’s a breakdown of our data validation processes and the stakeholders we engage with during our primary research:
- Supply Side Analysis: We initiate a supply side analysis by directly contacting market participants, through telephonic interviews and questionnaires containing both open-ended and close-ended questions. We gather information on their portfolios, segment revenues, developments, and growth strategies.
- Demand Side Analysis: To gain insights into adoption trends and consumer preferences, we reach out to target customers and users (non-vendors). This information forms a vital part of the qualitative analysis section of our reports, covering market dynamics, adoption trends, consumer behavior, spending patterns, and other related aspects.
- Consultant Insights: We tap into the expertise of our partner consultants from around the world to obtain their unique viewpoints and perspectives. Their insights contribute to a well-rounded understanding of the markets under investigation.
- In-House Validation: To ensure data accuracy and reliability, we conduct cross-validation of data points and information through our in-house team of consultants and utilize advanced data modeling tools for thorough verification.
The forecasts we provide are based on a comprehensive assessment of various factors, including:
- Market Trends and Past Performance (Last Five Years): We accurately analyze market trends and performance data from preceding five years to identify historical patterns and understand the market’s evolution.
- Historical Performance and Growth of Market Participants: We assess the historical performance and growth trajectories of key market participants. This analysis provides insights into the competitive landscape and individual company strategies.
- Market Determinants Impact Analysis (Next Eight Years): We conduct a rigorous analysis of the factors that are projected to influence the market over the next eight years. This includes assessing both internal and external determinants that can shape market dynamics.
- Drivers and Challenges for the Forecast Period:Identify the factors expected to drive market growth during the forecast period, as well as the challenges that the industry may face. This analysis aids in deriving an accurate growth rate projection.
- New Acquisitions, Collaborations, or Partnerships: We keep a close watch on any new acquisitions, collaborations, or partnerships within the industry. These developments can have a significant impact on market dynamics and competitiveness.
- Macro and Micro Factors Analysis:A thorough examination of both macro-level factors (e.g., economic trends, regulatory changes) and micro-level factors (e.g., technological advancements, consumer preferences) that may influence the market during the forecast period.
- End-User Sentiment Analysis: To understand the market from the end-user perspective, we conduct sentiment analysis. This involves assessing the sentiment, preferences, and feedback of the end-users, which can provide valuable insights into market trends.
- Perspective of Primary Participants: Insights gathered directly from primary research participants play a crucial role in shaping our forecasts. Their perspectives and experiences provide valuable qualitative data.
- Year-on-Year Growth Trend: We utilize a year-on-year growth trend based on historical market growth and expected future trends. This helps in formulating our growth projections, aligning them with the market’s historical performance.
Research process adopted by TNR involves multiple stages, including data collection, validation, quality checks, and presentation. It’s crucial that the data and information we provide add value to your existing market understanding and expertise. We have also established partnerships with business consulting, research, and survey organizations across regions and globally to collaborate on regional analysis and data validation, ensuring the highest level of accuracy and reliability in our reports.